Networking in AWS is important to understand in order to keep sensitive servers and applications secured while still maintaining Internet connectivity. It can be quite different from traditional networks, and because there are similarly named pieces it can be difficult remember the differences and know how to properly use them. Three commonly confused services are Internet Gateways, NAT Gateways, and NAT Instances. To fully understand them, it is first necessary to understand some fundamentals.
Public Subnets
When building multi-tier applications or microservices, some applications and services will likely need to be exposed to incoming traffic from the Internet. However, many of backend processes may only need access the Internet, and not allow inbound traffic. Implementing this type of architecture can be accomplished by having externally exposed services in a “public subnet” and everything else in a “private subnet.”
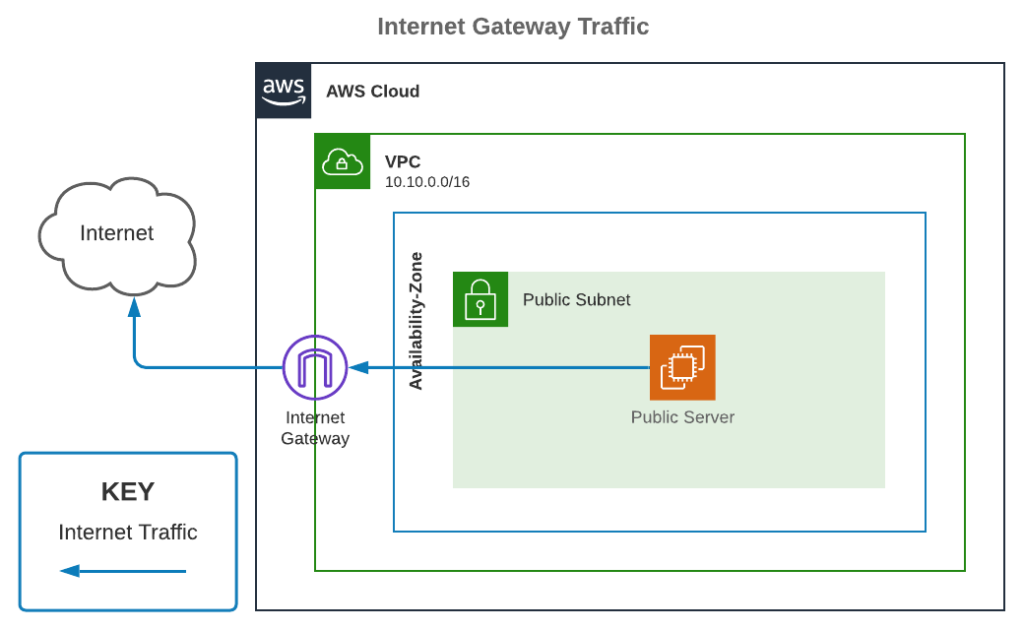
A public subnet is any subnet that has a route to an Internet Gateway. The allows traffic directed for the Internet to have a path out, and for inbound Internet traffic to be routed to the services in the subnet.
Note: Typically, this route will be a “default” route – that is, one with a destination of “0.0.0.0/0”.
Note: Despite common misunderstanding, having auto-assigned public IP addresses in a subnet does not make a subnet public – though it is common as having a public IP address is needed for inbound Internet traffic.
So what is an Internet Gateway?
Internet Gateway
An Internet Gateway is a VPC component that allows communication between the VPC and the Internet. They are horizontally scaled, redundant, and highly available.
As its name implies, it’s like a router on the edge of a network. Without an Internet Gateway, nothing in a VPC can access the internet, even with a public IP address. There is no charge with Internet Gateways, and it is only possible to one per VPC. Additionally, an account’s default VPC already has one of these.
Private Subnets
A private subnet is any subnet that doesn’t have a route to an Internet Gateway (that is, any subnet that is not public). As a result, they have no means to communicate with the Internet. This is where NAT Gateways and Instances come in to play, they allow a private subnet access to the Internet.
We’ll start with NAT Gateway, as it will make understanding NAT Instances easier.
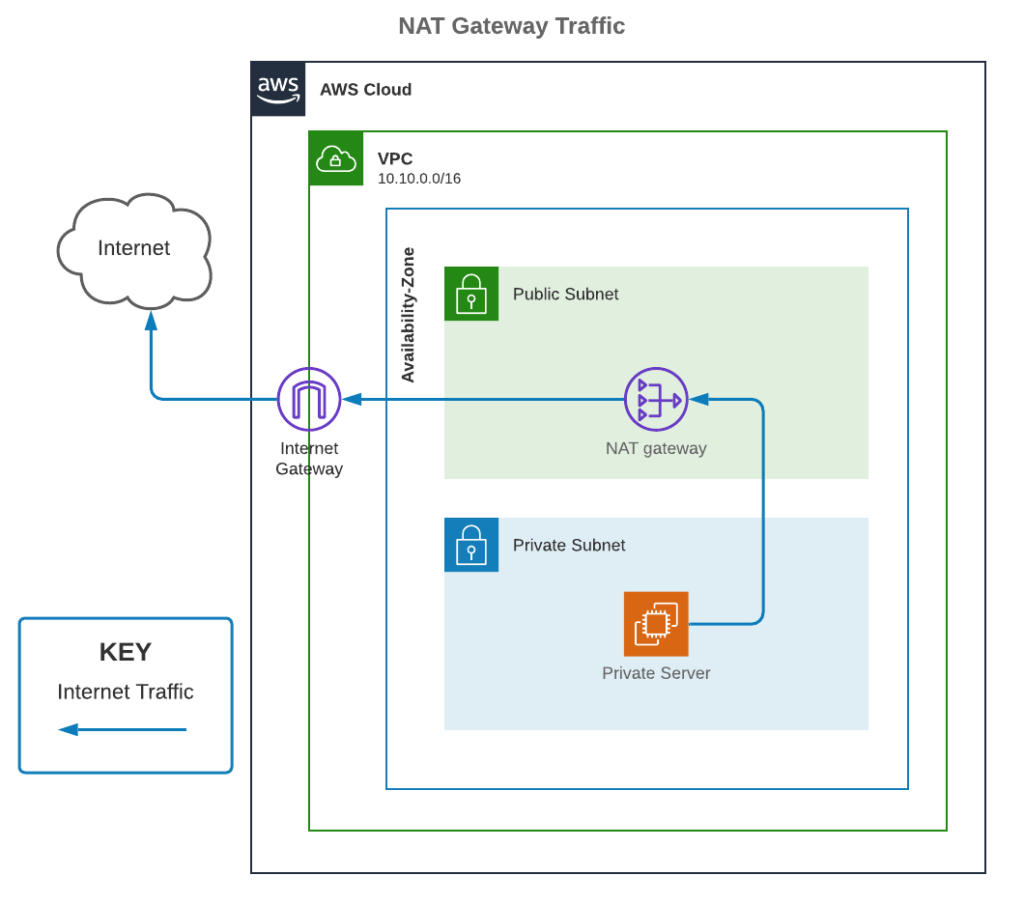
NAT Gateway
A NAT Gateway is an AWS service that allows a private subnet to have access to the Internet, but prevents the Internet from initiating a connection directly to the instances.
While the NAT Gateway is needed for private subnets to have Internet access, it is created in a public subnet. Unfortunately, it has an hourly cost unlike Internet Gateways.
Because they are deployed into a single availability zone, to ensure high availability it is best to deploy one per availability zone and configure routing to use the NAT Gateway in the same availability zone.
To use the NAT Gateway, assign a route in the private subnet, in lieu of a route to an Internet Gateway. Traffic destined for the Internet will flow from the private subnet to the NAT Gateway in the public subnet, and then out to the Internet through the Internet Gateway.
NAT Instance
Unlike NAT Gateway and Internet Gateway, a NAT Instance is not a special service offered by AWS. It is just a term for when using an EC2 instance to perform NAT Gateway-like functionality. It is similar to hosting database software on an EC2 instance rather than using Amazon RDS.
Because it is a self-managed instance, configuring routing, updating the software and operating system, and right-sizing instances is the responsibility of the owner. It is generally not recommended unless there is a specific use-case that needs to support this customization.
Similar to a NAT Gateway, a NAT Instance will need to be in a public subnet, and a private subnet will need a route to the NAT Instance to have internet access.
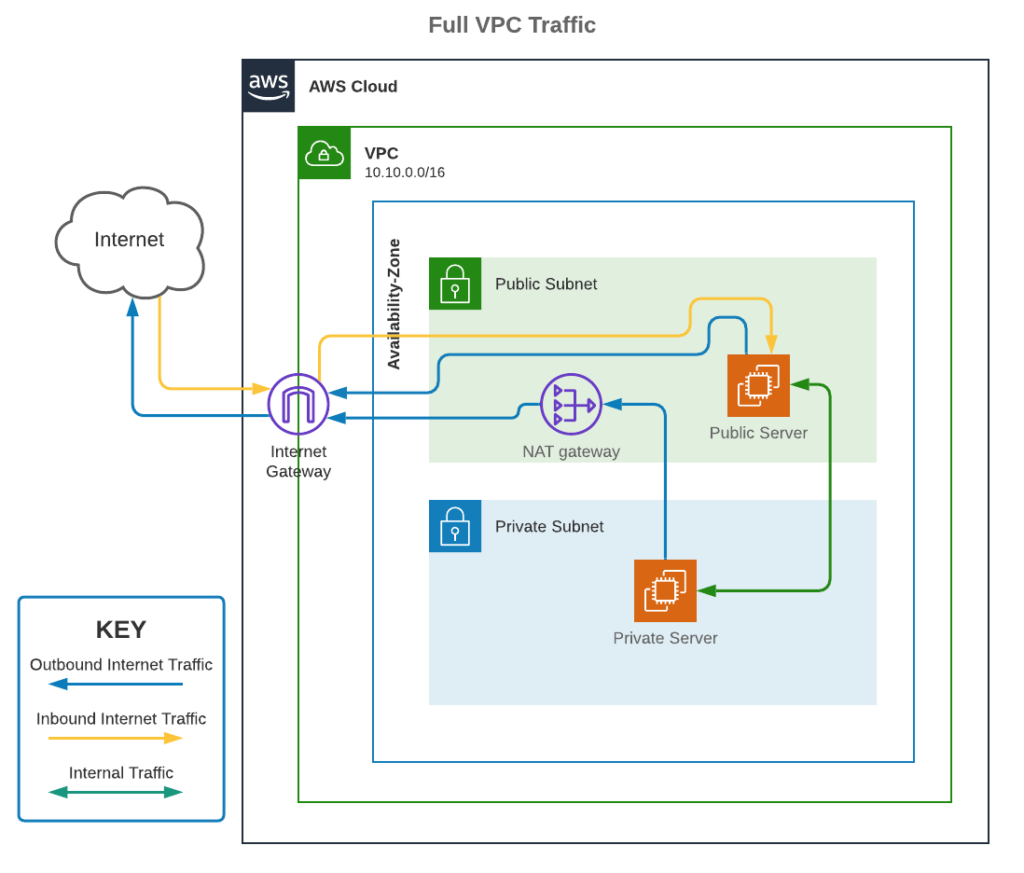
Putting it together
To help put it all together, here’s the bigger picture connecting all the parts in a common environment.
For a public subnet to have Internet access, inbound and outbound, an account needs:
- Internet Gateway attached to a VPC
- Route to the Internet Gateway in the attached route table
- Instances have public IP addresses (auto-assigned or attached Elastic IP address)
- Appropriate security group and NACL allowances
For a private subnet to have Internet access, the following will provide outbound Internet access but not inbound:
- Internet Gateway attached to a VPC
- NAT Gateway or Instance in a public subnet in the same VPC
- Route to the NAT Gateway or Instance in the private subnet’s attached route table
- Appropriate security group and NACL allowances
Conclusion
Hopefully this provides a clearer understanding of the differences between the Internet Gateway, NAT Gateway, and NAT Instances on AWS. Additionally, this should have illustrated the difference between public and private subnets, and how to use the private subnet to block external connections to more secure servers and applications.
If you would like to read in greater detail about this topic, here are some links to AWS Docs on the discussed topics.
- Internet Gateways and Private vs Public Subnets: https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Internet_Gateway.html
- EC2 Instance IP Addresses: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-instance-addressing.html
- NAT Gateway and NAT Instance Comparison: https://docs.aws.amazon.com/vpc/latest/userguide/vpc-nat-comparison.html







[…] AWS Quick Tips: Internet Gateways, NAT Gateways, and NAT Instances […]