If you’re looking to get started with AWS, Uturn’s Director of Engineering David Matthews is a great person to give you that help. In this short series of articles, he will help you with understanding the requirements around building the foundation for your new cloud environment and then deploying your initial VPC with Hashicorp’s Terraform.
AWS networking all starts with the AWS VPC, Virtual Private Cloud. This service is the centerpiece of your networking stack in AWS. When building your first AWS environment it is easy to overlook many configuration considerations. Things like:
- How large of a CIDR is required, for the VPC, per subnet?
- How many AZs should I use?
- How many subnets do I need?
- How many subnets should be public?
Many of these questions don’t have a one size fits all answer. This will vary greatly depending on your requirements. However, let’s tackle each, one at a time.
How large of a CIDR is required?
This is a HUGE question. As it depends on, what are you putting in this VPC. If you are utilizing Lambda inside of the VPC or containers on ECS or EKS then there could be a large requirement for IPs. However, if you are building out dozens of accounts then maybe you need a smaller chunk per account. My suggestion is always considering a multi-account strategy and building smaller CIDRs per account. We have found that in most cases an account does not require a huge block of IPs, and a /20 per account works quite well. Another way to look at the range would be to dedicate a specific range of IPs to AWS, say a /13, and then determine the number of accounts you believe you will need over the next 3 years and make sure that the CIDR per account * num of accounts is less than you max AWS CIDR range.
How many AZs should I use?
The Uturn standard is 2 AZs, unless there is a requirement for 3 AZs, like utilizing Managed Kafka Service (MSK). 2 AZs is often enough for DR and does not split your subnets too small.
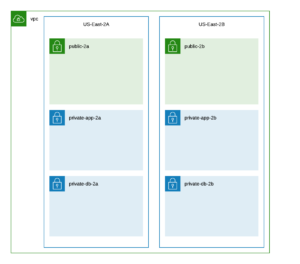
How many subnets do I need?
Uturn recommends a simple network, with just 3 subnets per AZ (Public, App, DB). This is due to the fact that most organizations have a difficult time managing multiple networks and with AWS Security Groups handling instance firewalls, there is less of a requirement for segmenting the network into a large number of subnet-based security zones. With a 3 subnet per AZ configuration and a /20 CIDR per VPC it allows for the follow IP configuration:
- Public Subnet (AZ1, AZ2) – /24 each
- AZ1 – 256 IPs
- AZ2 – 256 IPs
- App Subnet – /22 each
- AZ1 – 1024 IPs
- AZ2 – 1024 IPs
- DB Subnet – /24 each
- AZ1 – 256 IPs
- AZ2 – 256 IPs
This configuration does not work for all environments, as there are some environments that require more public IPs, or DB IPs. However, if you are looking for a generic setup, this is the way to go.
How many subnets should be public?
There should only be 1 public subnet per AZ, unless your environment truly requires something different.
With these suggestions your base VPC configuration would look something like this: